Table of Contents
ToggleWhat is Private Key Crypto?

Features of Private Key Crypto
- The Private Key comprises characters in uppercase, lowercase, and numeric forms.
- The intricate arrangement of characters within the Private Key is the result of random intermixing and swapping, without following any specific pattern. This characteristic poses a significant challenge for hackers attempting to breach a user’s assets.
- Each Private Key possesses the capability of producing a unique address that facilitates the execution of transactions within a wallet.
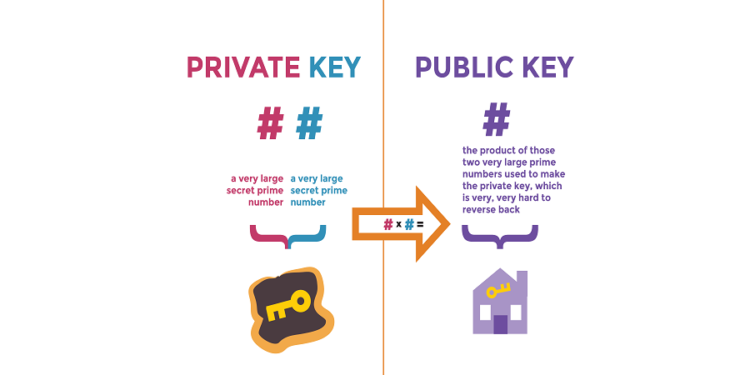
What is Public Key?
In essence, Public Key is a character string used to decrypt messages in an algorithm, but it can be widely distributed. An elementary example of Public Key is a user’s wallet address. The Public Key has the following form: 3048 0241 00C9 18FA CF8D EB2D EFD5 FD37 89B9 E069 EA97 FC20 5E35 F577 EE31 C4FB C6E4 4811 7D86 BC8F BAFA 362F 922B F01B 2F40 C744 2654 C0DD 2881 D673 CA2B 4003 C266 E2CD CB02 0301 0001What is the difference between Public Key and
Private Key Crypto?

Public Key Crypto | Private Key Crypto |
| Grant permission for receipt of the cryptocurrency and identification of the associated account. It is possible for anyone to find a public key on the ledger of the blockchain. | To enable users to utilize coins during connection, the Private Key serves the purpose of proving ownership of the corresponding public key. |
| Public | Must keep it a secret |
| It is not possible to derive a Private Key from a Public Key. | It is possible to derive the Public Key from the Private Key. |
| The disclosure of one’s Public Key has no bearing on the assets belonging to the individual concerned. | In the event that the Private Key is exposed, there is a risk of permanent loss of the assets. It is essential to carefully safeguard the Private Key to prevent any potential unauthorized access or breach. |
| The shortened version of Public Key is commonly referred to as an Address, which serves as a unique identifier for a wallet or account on a blockchain network. | There is no shortened version |
Mechanisms and algorithms
There are two distinct types of keys used for encryption and decryption in Public Key systems. The Public Key is available to anyone, whereas the Private Key is only accessible by its rightful owner. In an exchange between two parties, a symmetrical key is generated. This symmetrical key, known as the Private Key, is shared between the sender and the receiver via an encrypted message.Efficiency
There exists a difference in the authentication speed between Private Key and Public Key. In this regard, Private Key only requires one key whereas Public Key necessitates two keys.Privacy ability
The Private Key is known for ensuring excellent privacy for its owner; however, losing the Private Key would result in the inability to recover and access encrypted files. The complexity of this type of key also makes it challenging to remember, as it is a combination of complex numerical sequences. On the other hand, the Public Key is easy to remember and locate, without any risks associated with key loss.Digital signatures
The Private Key can serve as an electronic signature while the Public Key is used for verification. The use of electronic signatures provides several security benefits, including verifying the legal identity of the user and ensuring the integrity of the message.Encryption and Decryption
The Public Key plays a critical role in encryption, while the Private Key is capable of decrypting encrypted information. In other words, the Private Key can decrypt messages that have been converted. Typically, the Public Key is utilized in protocols, system software, or applications to ensure security in the online space.How Public Key & Private Key work
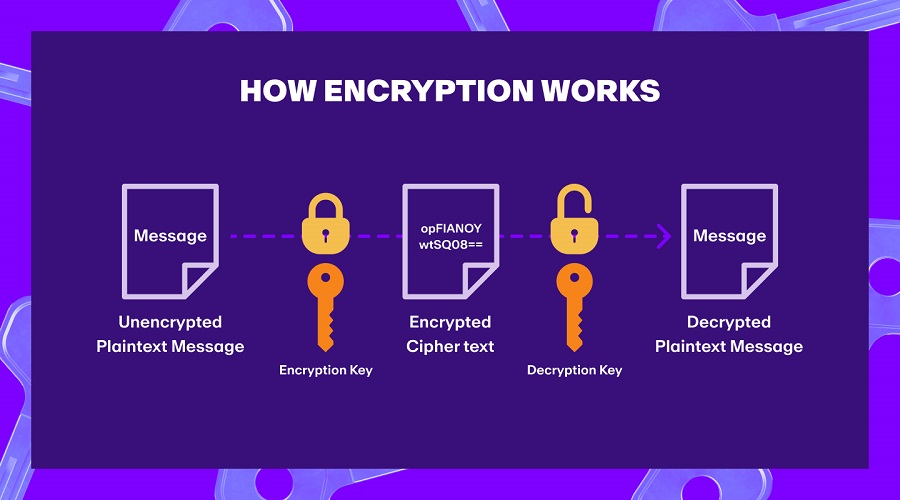
- The transaction is encrypted using the public key of the recipient and decrypted using the accompanying private key.
- Upon completion of the transaction, a signed agreement will be provided as evidence that no modifications were made. The sender will electronically sign the transaction to demonstrate their ownership rights to the specified amount of assets.
- The transaction is eventually uploaded onto the Blockchain and automatically verified by Nodes. If the transaction fails to be verified, the network will reject it. However, if the transaction is successfully processed and confirmed, it is recorded on the Blockchain ledger and cannot be tampered with. At this point, the assets are sent to the designated Public Key of the receiver. The entire process serves as an automated means of verification and authorization for secure and trustworthy transactions within the network.
For example:
In order to transfer 1 BTC from Person A to Person B, Person A must obtain the Public Key of Person B to encrypt it with the amount to be transferred. Subsequently, Person A signs the transaction and sends it to the Blockchain. Upon successful encryption and verification of the transaction, Person B receives the 1 BTC sent by Person A. Person B will then need to use their Private Key to decrypt and utilize this BTC. In this scenario, if there are attackers who attempt to breach the server and steal the BTC amount, they will be unable to do so as they lack the Private Key. The decryption of the transaction is only possible by person B who solely possesses the Private Key.Public Key & Private Key in Crypto

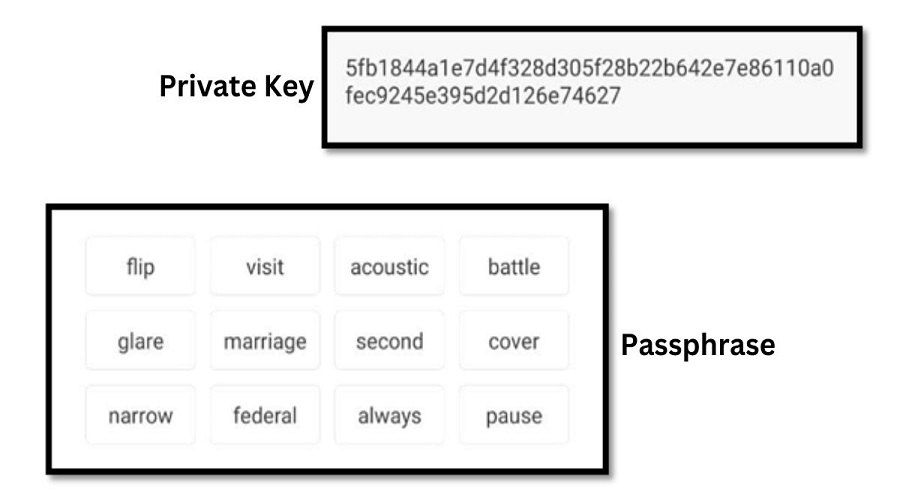
What is a passphrase?
A passphrase typically consists of 12 to 24 characters used for encryption, such as the string, “lecture estate tube tunnel decade tone flash army pink nice net trap.”What do Passphrase and Private Key Crypto have in common?
The common purpose of Private Key and Passphrase is to ensure the security of one’s account. It is possible to use both types of cryptography to gain access to a wallet or to recover one. Furthermore, due to their length and complexity, both Private Key and Passphrase offer superior security compared to regular Passwords.Difference between Passphrase and Private Key Crypto
Pros and cons of Private Key Crypto
The Public Key, Passphrase, and Private Key all play distinct roles in enabling secure, convenient, and efficient transactions and asset storage. Of these, the Private Key assumes a critical function with regard to each individual wallet or transaction. The Private Key offers distinct advantages in terms of privacy and security, which are almost absolute. Nevertheless, its limitation lies in its myriad random characters that make it challenging for individuals to commit to memory. It is therefore imperative not to disclose this information to anyone and to safely store it using secure methods to avoid potential loss or forgetfulness.How to secure Private Key safely

The fundamental premise of asset storage within any type of wallet is that the assets themselves remain on the Blockchain network, while the holder maintains control only via their private key. As such, the most secure approach to protecting one’s assets is to ensure absolute confidentiality of one’s private key.
The security level for hot wallets is not high due to their continuous connection to the Internet, thus providing hackers with ample opportunities to attack users’ assets. Hackers can target hot wallets, laptops, PCs, phones, or any other devices connected to the Internet. Therefore, to minimize the risk of asset theft, users must refrain from storing private keys on devices connected to the Internet and should instead opt for offline methods such as storing private keys in a physical notebook or storing them on other offline devices. In short, users must prioritize the security of their digital assets by adopting secure measures like storing private keys offline to protect themselves from potential attacks. With regards to cold wallets, the level of security is heightened as the device can disconnect from the internet when not in use. However, its limitation lies in the possibility of loss, damage, or malfunction of the physical wallet, rendering it unusable. In order to avoid such situations, it is crucial to store the recovery keywords in a safe place for account restoration when necessary. These keywords are provided upon wallet creation. Similarly, for hot wallets, it is advisable to record this information in a secure ledger, refraining from storing it on internet-connected devices or taking pictures of the recovery keywords. Additionally, it is recommended to have two cold wallets to guarantee immediate backup in case of device failure.Other commonly utilized techniques include Bookmark or Google Authenticator, among others.
With the shared information, it is likely that you have gained a fundamental understanding of what Private Key is, as well as the differences between Private Key, Public Key, and Passphrase. From there, it is hoped that you will discover appropriate methods for storing your codes while grasping the roles of each key type in relation to your assets.What is Yield Farming? Gain a comprehensive understanding of the terminology associated with Yield Farming
The concept of Yield Farming, prominent Yield Farming platforms, and the associated risks and opportunities are explored in this article,...
Read moreWhat is Initial DEX Offering (IDO crypto)? Does playing IDO really give you a 100% chance of winning?
One may inquire as to why the Initial DEX Offering (IDO) has gained widespread popularity and whether investing in IDO...
Read moreWhat is ERC – 20? Advantages, disadvantages & how to create ERC- 20 network tokens
In this article, we will explore ERC-20 and ERC-20 tokens along with their applications and advantages and disadvantages. For those...
Read moreWhat is Airdrop Crypto? Instructions for making airdrop coins in the Crypto market
What is Airdrop and how many forms of Airdrop Crypto exist? Discover the limitations and effective instructions on how to...
Read moreWhat is DAO? Limitations and Investment Potential of DAO in Crypto
Understanding the terminologies used in the field of cryptocurrency is crucial for individuals involved in Crypto market participation or intending...
Read moreWhat is zkEVM? Classification of groups zkEVM
ZkEVM is an abbreviation for the term "Zero-Knowledge Ethereum Virtual Machine". It is a protocol that enables the execution of...
Read moreWhat is web3 technology? How to invest in Web3 in 2023
The emergence of Web 3.0 following Web 2.0 has brought about increased flexibility and superior interaction capabilities compared to its...
Read moreWhat is move to earn? best move to earn crypto in 2023
In the current GameFi market, it is possible to combine the seemingly unrelated tasks of earning money and improving one's...
Read moreWhat does NFT crypto stand for: Clarifying the Significance of Non-Fungible Tokens (NFTs) through technical examination
Non-fungible token (NFT) art are digital assets stored on a blockchain that depict physical or non-physical items, such as digital...
Read moreWhat are play to earn (P2E) Games? How to earn money with play game crypto?
Play to Earn has emerged as a popular trend in mid-2021, leading to a notable increase in the activity of...
Read moreWhat is an oracle in blockchain? Top blockchain oracle projects 2023
The intended function of blockchain technology was never to operate in isolation from the larger economic ecosystem. Despite the challenges...
Read moreBinance account sign up: What is binance account? how to create binance account?
Numerous cryptocurrencies are supported by Binance and its proficiency in ensuring swift exchange operations between volatile coins and fiat currencies...
Read moreWhat is a defining feature of the Metaverse Crypto? What does the term Metaverse refer to?
We have heard numerous prominent figures, such as Mark Zuckerberg, CEO of Facebook, and Satya Nadella, CEO of Microsoft, expound...
Read moreWhat are AI Tokens? Best AI Coins & Tokens to Invest in
The predicted impact of artificial intelligence (AI) is expected to revolutionize various sectors, including the field of cryptocurrency. The AI...
Read moreWhat are Fan Tokens? How Binance Fan Tokens are Revolutionizing the World of Sports and Entertainment?
The Fan Token is a term that has been shared by the CEO of the cryptocurrency exchange CZ on Twitter,...
Read more